Suchen Sie etwas anderes?
Telnet configuration parameters start with a “TELNET” prefix. Telnet is recommended to remotely send AT commands, to change some configuration parameters or to find out the status of the remote modem with MTX-Tunnel. It is important to understand that Telnet will only work if the GPRS link has been established previously.
You can see TELNET in a MSDOS console or with specific software.
Table of Contents
TELNET_enabled
Description: This command enables Telnet services in MTX-Tunnel.
Possible values:
- on, off
- Default value: off
Additional notes:
- MTX-Tunnel only supports 2 socket servers simultaneously. This means that Telnet cannot be enabled if MTX-Tunnel is working in server mode (MTX_mode: server) and WebServer is active (WEBSERVER_enabled: on)
TELNET_login
Description: You can secure Telnet login with this command.
Possible values:
- Text string maximum 32 characters
- Default value: (none)
Additional notes:
- If you write the login and password string, MTX-Tunnel will ask for credentials in the remote TELNET connection. If you do not use this feature, an anonymous connection will be created and there will be access without restriction after connection
- It is recommended to use login and password access security if TELNET_firewall is disabled (“off” value)
TELNET_password
Description: This command is used to specify a Telnet login password.
Possible values:
- Text string maximum 32 characters
- Default value: (none)
Additional notes:
- If you enable login & password parameters, those who want to gain access will be asked for it when a remote Telnet connection is established. If you disable this feature (no value in login and password), you will have direct access to Telnet after connection
- It is recommended to use (enable) the login & password parameters if the TELNET_firewall parameter is “off”
TELNET_loginGuest
Description: It specifies the username in order to access the MTX-Tunnel telnet server as a guest.
Possible values:
- Text string maximum 32 characters
- Default value: (none)
Additional notes:
- Under the Guest user it won’t be possible to use commands like AT^MTXTUNNEL= so it won’t be possible to read or change the MTX-Tunnel configuration. This user can execute supervision commands like AT+CSQ to check the coverage, AT+CFUN=1,1 to execute a remote reset, etc
- This user won’t be available if we don’t specify the username and password
TELNET_passwordGuest
Description: It specifies the password to be able to access the MTX-Tunnel telnet server as a guest.
Possible values:
- Text string maximum 32 characters
- Default value: (none)
Additional notes:
- Under the Guest user it won’t be possible to use commands like AT^MTXTUNNEL= so it won’t be possible to read or change the MTX-Tunnel configuration. This user can execute supervision commands like AT+CSQ to check the coverage, AT+CFUN=1,1 to execute a remote reset, etc.
- This user won’t be available if we don’t specify the username and password
TELNET_firewall
Description: This command enables Telnet firewall. If firewall is enabled it will only accept remote connections from specific authorized IP addresses -see FIREWALL IP1 command-. If disabled, any IP address can remotely connect to MTX-Tunnel using Telnet.
Possible values:
- on, off
- Default value: on
Additional notes:
- If firewall is disabled (value= “off”), it is recommended to use a login and password to avoid unauthorized access
TELNET_port
Description: TCP port used in MTX-Tunnel Telnet server.
Possible values:
- 1… 65535
- Default value: 23
Additional notes:
- Do not use the same TCP port in command TCP_port and/or WEBSERVER_port
- If you are planning to use SIM card with public IP, TCP port 23 is not recommended. It is better to use another port like 20023. The reason is to avoid unnencessary data traffic
TELNET_bypass
Description: this parameter is only allowed for 2G models (MTX-65i family). All 3G models can implement 2 gateway 2G/3G – Serial with parameters TCP_port and TCP_port2. Parameter NOT recommended. Only used for compatibility reasons. This parameter enables the use of TELNET as a bypass connection to control the device connected to the MTX-Tunnel modem’s COM serial port. In other words, this can allow 2 simultaneous Serial-GPRS tunnels and control two connected pieces of equipment, one to COM1 and other to COM2
Possible values:
- on, off
- Default value: off
Additional notes:
- If enabled TELNET_login and TELNET_password parameters will be used
TELNET_instances
Description: This parameter allows you to have more than one simultaneous active Telnet sessions. Firmware versions prior to the version 9.12 do not allow it. You may dispose of up to two simultaneous active Telnet sessions.
Possible values:
- 1, 2
- Default value: 1
Additional notes:
- It is not recommended to use this parameter unless it is absolutely necessary for the application. The reason is not to subtract memory and CPU resources from MTX-Tunnel unnecessarily
TELNET_auth
Description: This parameter allows you to increase security during the authentication phase of a Telnet session. When using the options “otp” (One Time Password) and “otpsms” (One Time Password SMS) you can enjoy a higher level of security compared to “std” (standard) provided by Telnet. The “otp” and “otpsms” options are available from MTX-Tunnel v9.20 onwards.
Possible values:
- std otp, otpsms
- Default value: std
Additional notes:
- When choosing the “std”option, you run the standard authentication process of a Telnet session, where the username (TELNET_login parameter) and a password (TELNET_password parameter) to be authenticated are sent to the remote modem
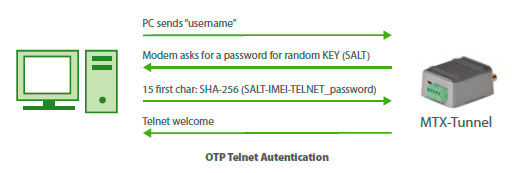
- When choosing the “otp” option,the password used in a remote modem is always variable, which makes it much less prone to be intercepted. The password can be used only once. The authentication process is as follows. After you have entered a username, the modem will require the password for a certain code, always randomly generated, indicated in brackets.
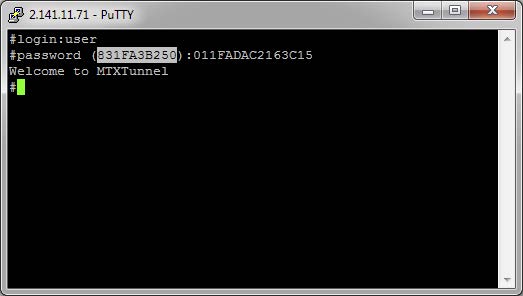
- As a response to this password the first 15 HASH characters generated by SHA-256 and corresponding to random-IMEI-Telnet_password should be returned. That means, as it is shown in the example, that if the returned random password is 831FA3B250, the IMEI of the modem is 357042060366409, and if the Telnet Password is 1234, the HASH to be returned as a password is 011FADAC2163C15, just as it can be seen in the following example:
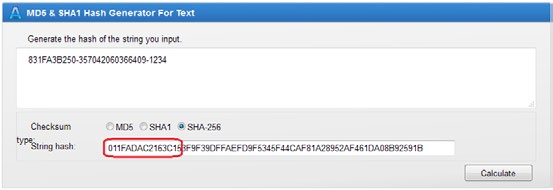
- This way the Password is never compromised, because the password is never sent through the Internet
- Finally, there is “otpsms” option. The process also consists of receiving an otp password (One Time Password), but it is requested via SMS. If you send a message with the text “mtxtunnel at^mtxtunnel=otp” (or its corresponding alias), you will receive a SMS message with a one-time login password. To use this method, it is recommended to use authorized phone numbers, for example:
SMS_allPhones: off
SMS_validPhone1: +34666123456
…
This way only authorized phone numbers will be able to request their one-time password for Telnet. - Remember that you can activate firewall (FIREWALL_enabled: on) to be able to access Telnet only from authorized IPs . (FIREWALL_IPx)
- Finally, if you want, your can keep Telnet service inactive and activate it any moment via SMS messages sent from authorized phone numbers



 Enter the “ethernet” or “modem” connection type:
Enter the “ethernet” or “modem” connection type:
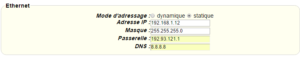
 For an ethernet configuration, make sure the IP parameters are compatible with server access according to the concentrator local network configuration. For an ethernet connection, the configuration must be compatible with the concentrator’s local network topology so that it can access the servers. This configuration is done from the “Networks” configuration page (see section 3.2.2.3: “Networks”).
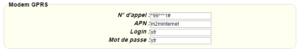
For a modem connection, the modem configuration must be correct before a connection can be set up. This configuration is done from the “Modem” configuration page (see section 3.2.2.4: “Modem”).
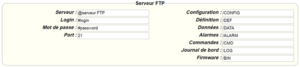
The parameters for the servers to be configured are at least the following:
For an ethernet configuration, make sure the IP parameters are compatible with server access according to the concentrator local network configuration. For an ethernet connection, the configuration must be compatible with the concentrator’s local network topology so that it can access the servers. This configuration is done from the “Networks” configuration page (see section 3.2.2.3: “Networks”).
For a modem connection, the modem configuration must be correct before a connection can be set up. This configuration is done from the “Modem” configuration page (see section 3.2.2.4: “Modem”).
The parameters for the servers to be configured are at least the following:
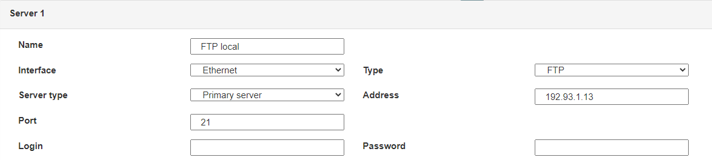 Therefore the following fields need to be configured: “Interface”, “Type”, “Server type”, “Address”, “Port”, “Login” and “Password”.
The other fields can be left at the default values subject to the directories having been properly created beforehand. See section 3.1.2: “Configuration files” for more details.
Therefore the following fields need to be configured: “Interface”, “Type”, “Server type”, “Address”, “Port”, “Login” and “Password”.
The other fields can be left at the default values subject to the directories having been properly created beforehand. See section 3.1.2: “Configuration files” for more details.



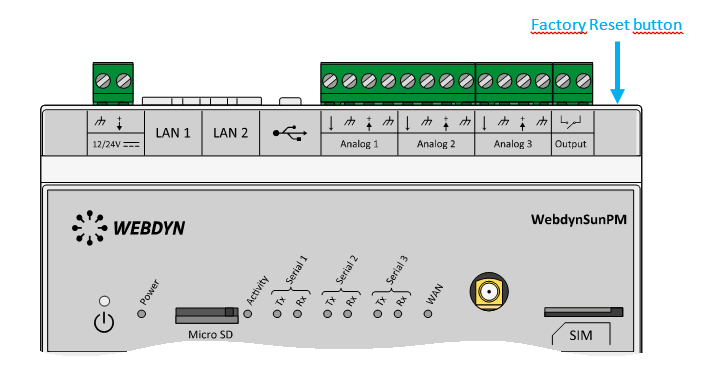 Wait. The concentrator will reboot using its factory configuration.
Wait. The concentrator will reboot using its factory configuration.