Suchen Sie etwas anderes?
Table of Contents
Introduction
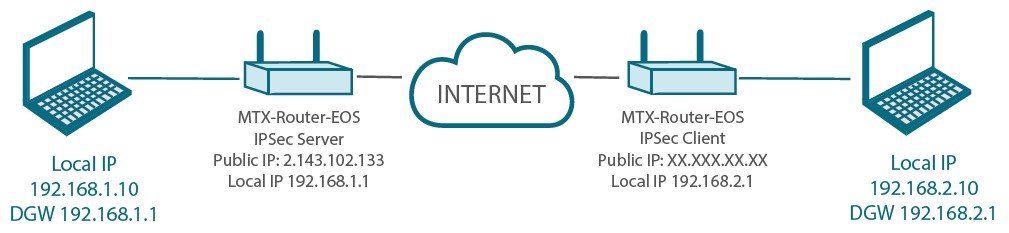
This application note will explain how to configure the MTX-Router-EOS in order to perform a client-server configuration using IPSec and shared key.
It is not part of this application note how to configure the network interfaces of the computers, nor windows firewall options and so on.
Server Configuration
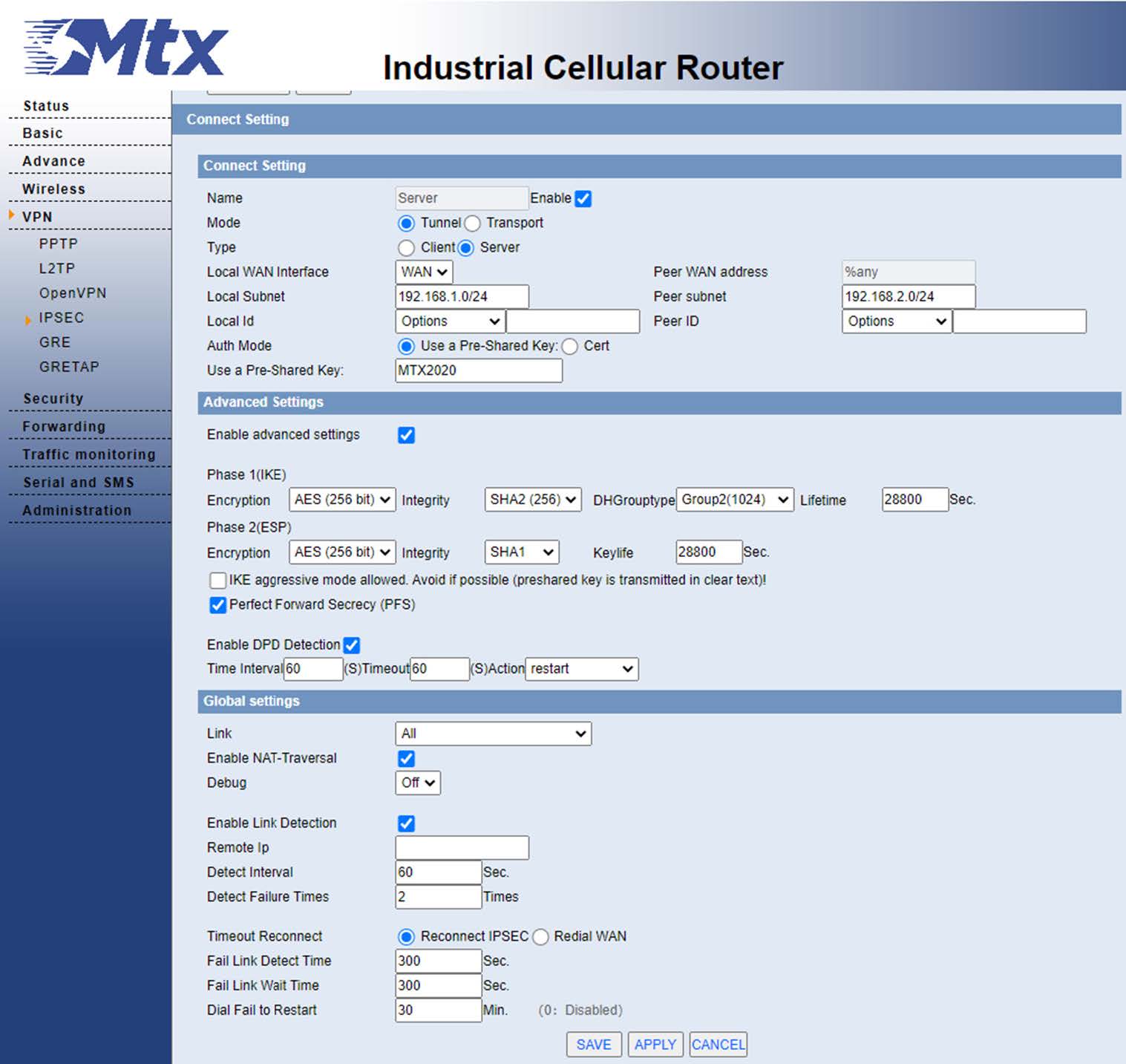
From the VPN -IPSec menu, we are going to configure the server options:
- We enable the IPSEC server and assign it the name we want to give it.
- We choose the mode, in this case tunnel.
- Then we configure the local subnet, in this case that of the server is 192.168.1.0/24 and that of the other is 192.168.2.0/24.
- As an identifier we have chosen to do so by taking your IP address.
- In this case we will establish the tunnel using a shared key.
- We will leave the rest of the options by default, apply and save.
OpenVPN client configuration
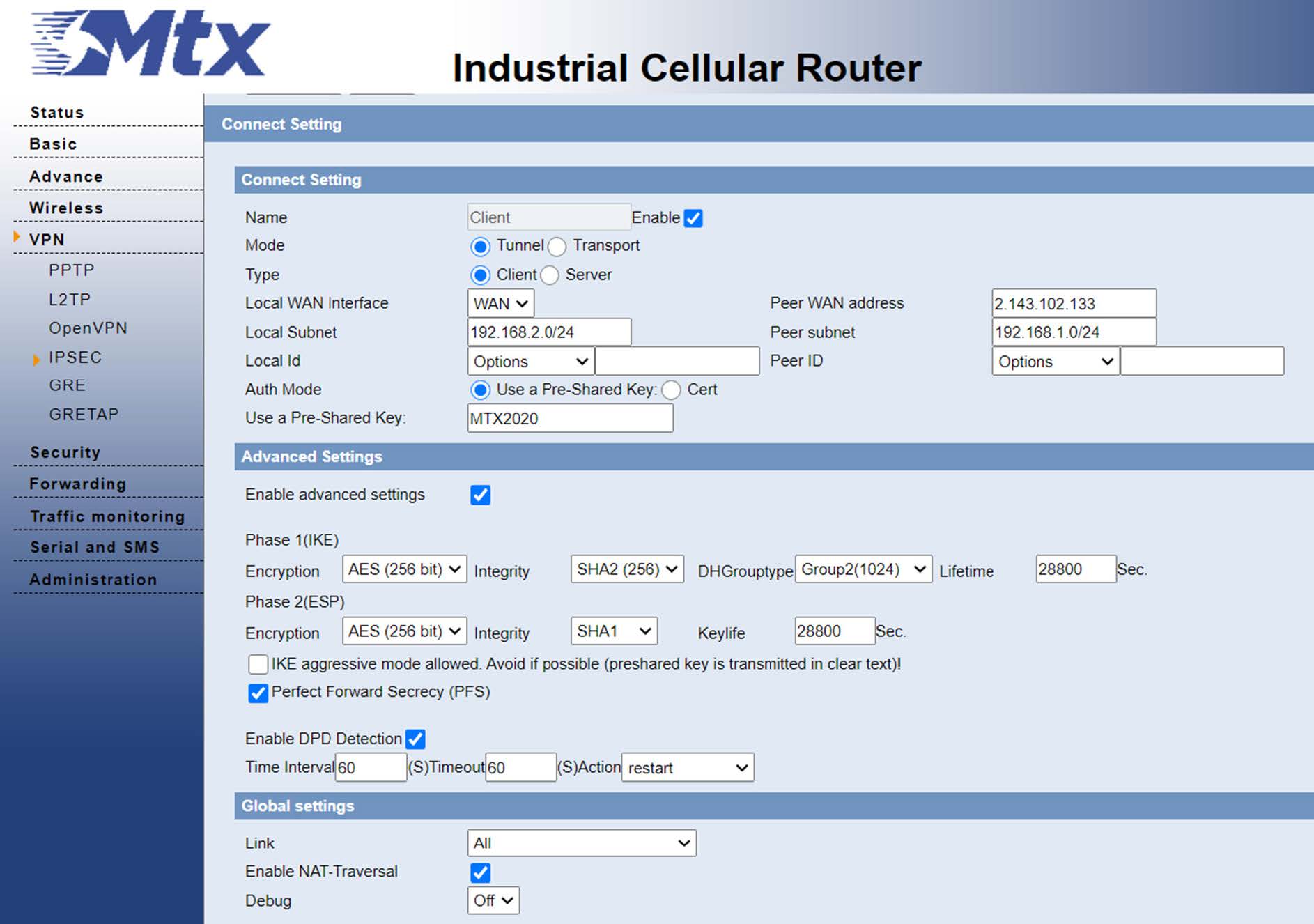
From the VPN -IPSEC menu, we are going to configure the client options:
- We enable the IPSEC client.
- We fill in the IP of the IPSEC server, in our case 2.143.102.133.
- The local subner for the client is 192.168.2.0/24 and the one for the server we have said is 192.168.1.0/24
- We fill in the pre-shared key that we have configured on the server, in this case MTX2020.
- We leave the rest of the options by default, apply the changes and save.
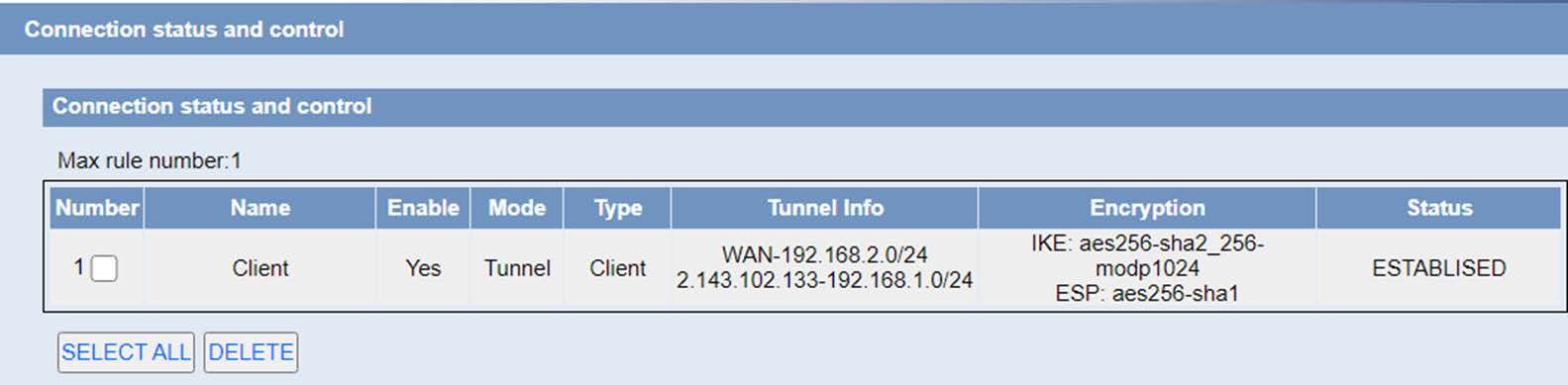
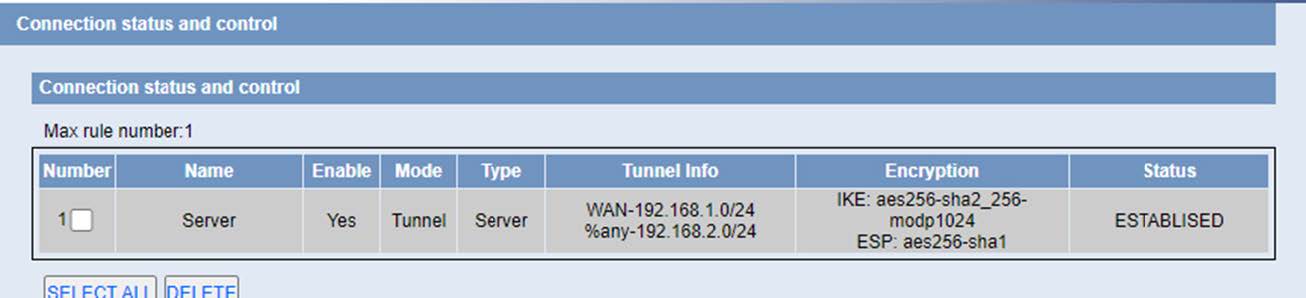
Once the changes are applied, we see how the tunnel appears as established:
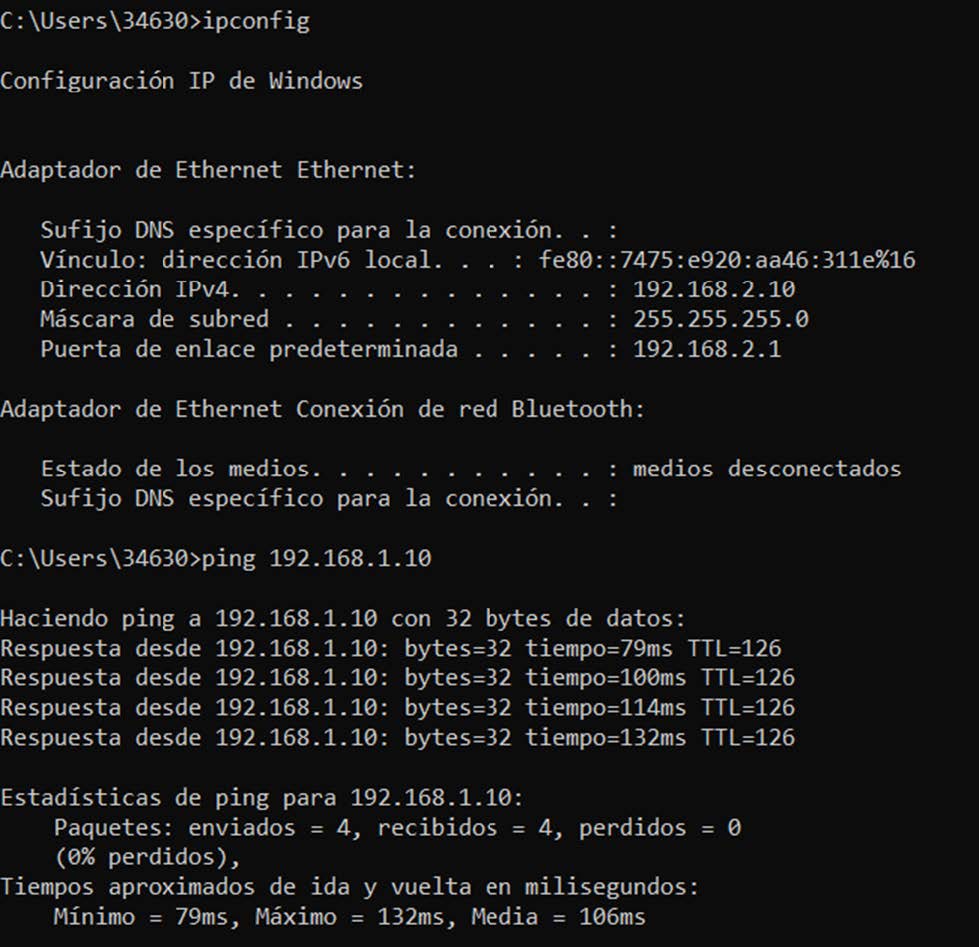
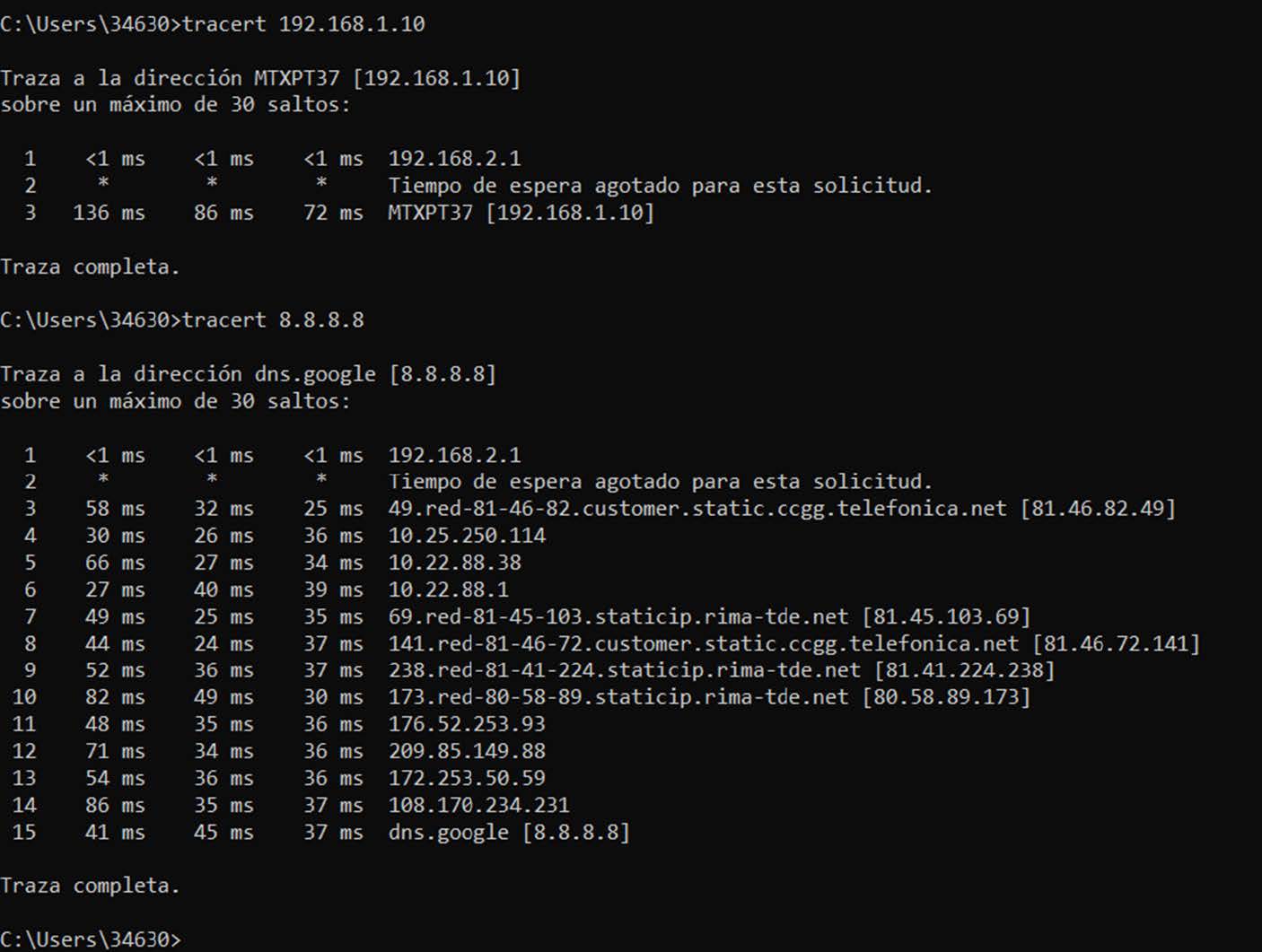
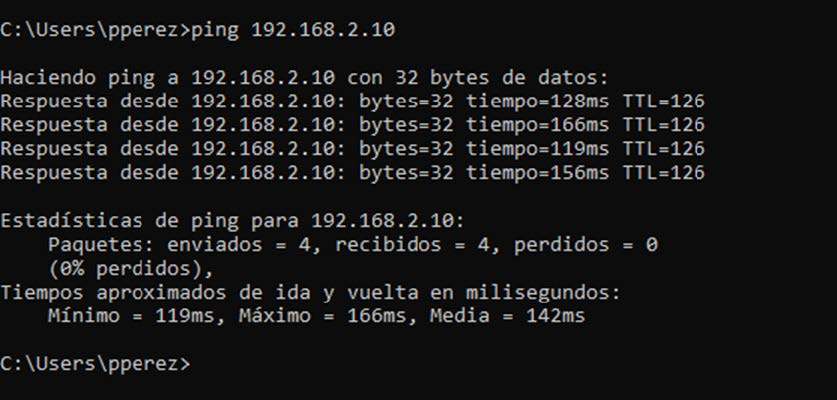
And we can ping the computer connected to the server:
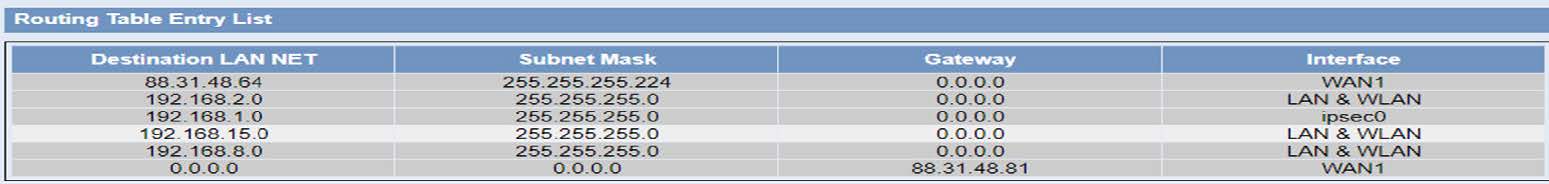
All the traffic to the subnet that hangs from the server will go out through the ipsec0 interface and the rest will go out through the WAN interface with the public IP of the telephone operator:
Similarly, from the point of view of the PC connected to the server, we can ping the client’s subnet:



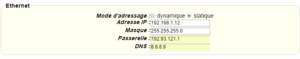
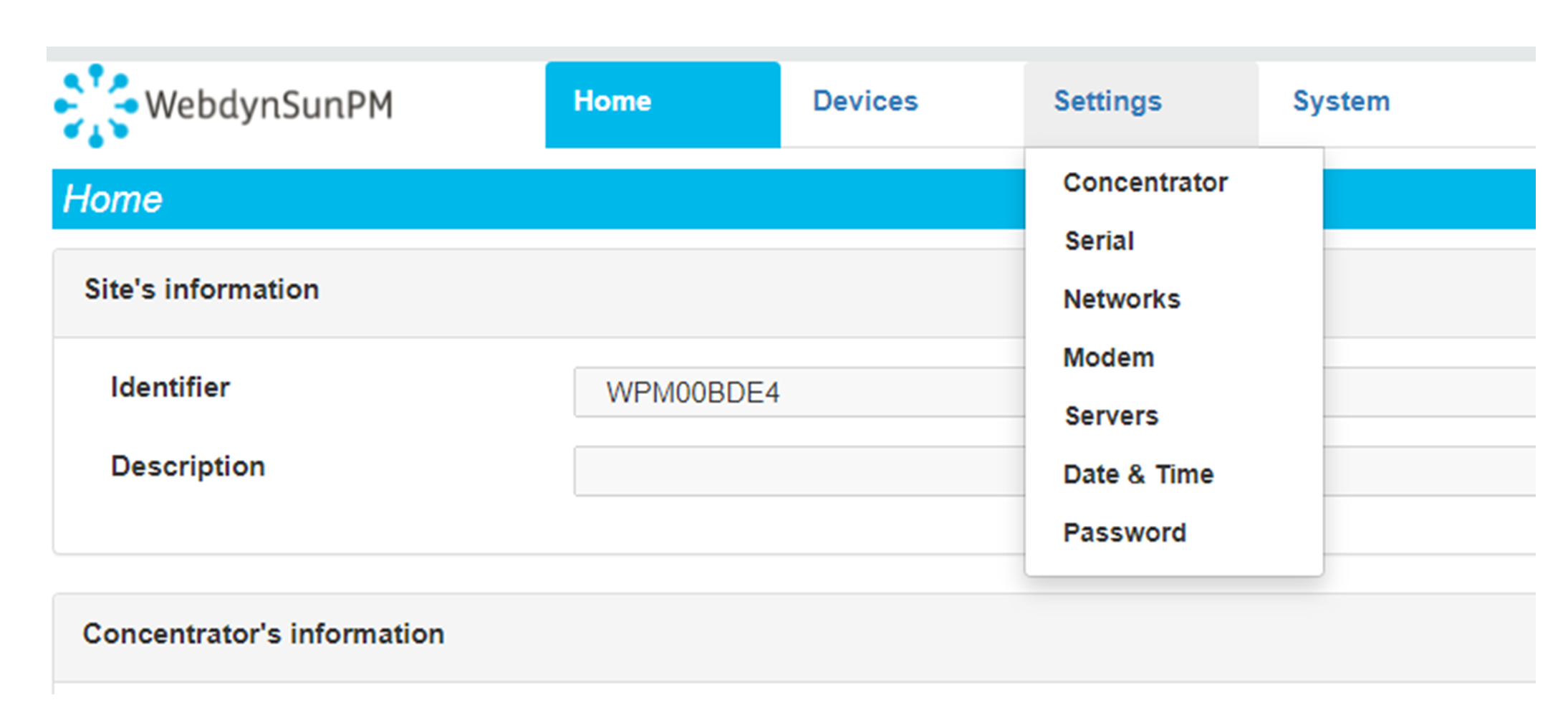 Enter the “ethernet” or “modem” connection type:
Enter the “ethernet” or “modem” connection type:
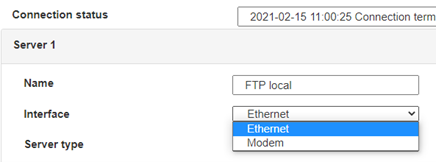 For an ethernet configuration, make sure the IP parameters are compatible with server access according to the concentrator local network configuration. For an ethernet connection, the configuration must be compatible with the concentrator’s local network topology so that it can access the servers. This configuration is done from the “Networks” configuration page (see section 3.2.2.3: “Networks”).
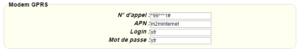
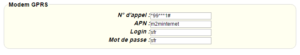
For a modem connection, the modem configuration must be correct before a connection can be set up. This configuration is done from the “Modem” configuration page (see section 3.2.2.4: “Modem”).
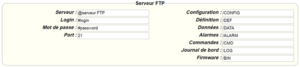
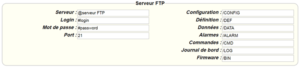
The parameters for the servers to be configured are at least the following:
For an ethernet configuration, make sure the IP parameters are compatible with server access according to the concentrator local network configuration. For an ethernet connection, the configuration must be compatible with the concentrator’s local network topology so that it can access the servers. This configuration is done from the “Networks” configuration page (see section 3.2.2.3: “Networks”).
For a modem connection, the modem configuration must be correct before a connection can be set up. This configuration is done from the “Modem” configuration page (see section 3.2.2.4: “Modem”).
The parameters for the servers to be configured are at least the following:
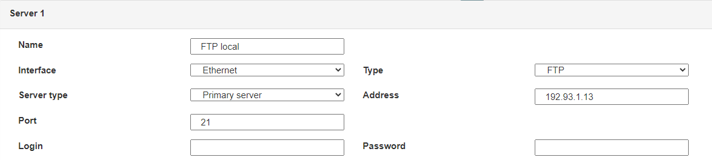 Therefore the following fields need to be configured: “Interface”, “Type”, “Server type”, “Address”, “Port”, “Login” and “Password”.
The other fields can be left at the default values subject to the directories having been properly created beforehand. See section 3.1.2: “Configuration files” for more details.
Therefore the following fields need to be configured: “Interface”, “Type”, “Server type”, “Address”, “Port”, “Login” and “Password”.
The other fields can be left at the default values subject to the directories having been properly created beforehand. See section 3.1.2: “Configuration files” for more details.



 Wait. The concentrator will reboot using its factory configuration.
Wait. The concentrator will reboot using its factory configuration.


 Esperar. El concentrador arrancará con su configuración de fábrica.
Esperar. El concentrador arrancará con su configuración de fábrica.


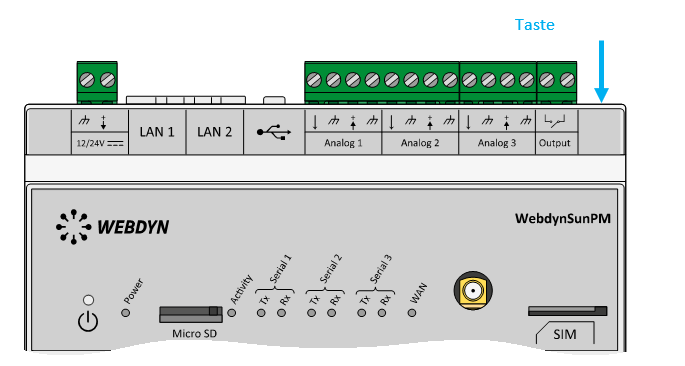 Warten Sie. Der Hub startet nach ein paar Augenblicken mit der Werkseinstellung neu.
Warten Sie. Der Hub startet nach ein paar Augenblicken mit der Werkseinstellung neu.

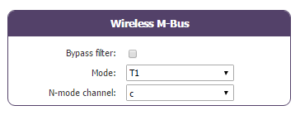

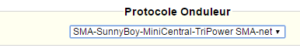

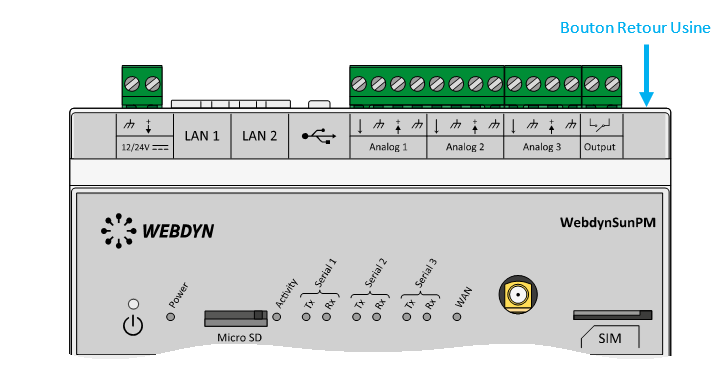 Attendre. Le concentrateur va redémarrer avec sa configuration usine.
Attendre. Le concentrateur va redémarrer avec sa configuration usine.
